Roadmap to Junior Pentester
The Chaos
Getting into penetration testing is exciting but it can also feel overwhelming. One quick search online and you’re hit with endless topics: networking, Linux, scripting, web apps, certifications, tools, exploits, and more. It’s easy to feel like you need to learn everything at once, which can be overwhelming. For many beginners, pentesting feels confusing, fragmented, and difficult to navigate.
At its core, pentesting is about understanding how complex systems work and how they can fail. Modern systems are built from many layers, and a pentester needs to understand several of them at once.
A single penetration test might involve:
- Networks and how data moves between systems
- Operating systems and how they manage users, processes, and permissions
- Web applications and how browsers interact with servers
- Databases and how data is stored and retrieved
- Security controls and how they are designed to stop attacks
The chaos is heightened when you hear advice such as:
- “Learn networking first”
- “Learn Linux”
- “Learn web security”
- “Learn scripting”
- “Just practice labs”
The hardest part of getting into penetration testing isn’t the technical difficulty—it’s the Chaos. There are too many topics, too many tools, too many opinions, and no obvious order to learn them in. Without structure, it’s easy to feel like you’re constantly busy but not actually progressing. All of this advice is technically correct—but without context, it feels overwhelming. Without strong foundations, learning can feel like memorizing random commands instead of developing real understanding.
This is where a roadmap becomes powerful.
A roadmap doesn’t just tell you what to learn. Over time, it helps you build your own methodology—a way of thinking and approaching problems that brings order to complexity. Following a structured roadmap builds skills step by step, ensuring that there are no knowledge gaps and brings order to the chaos.
The Roadmap
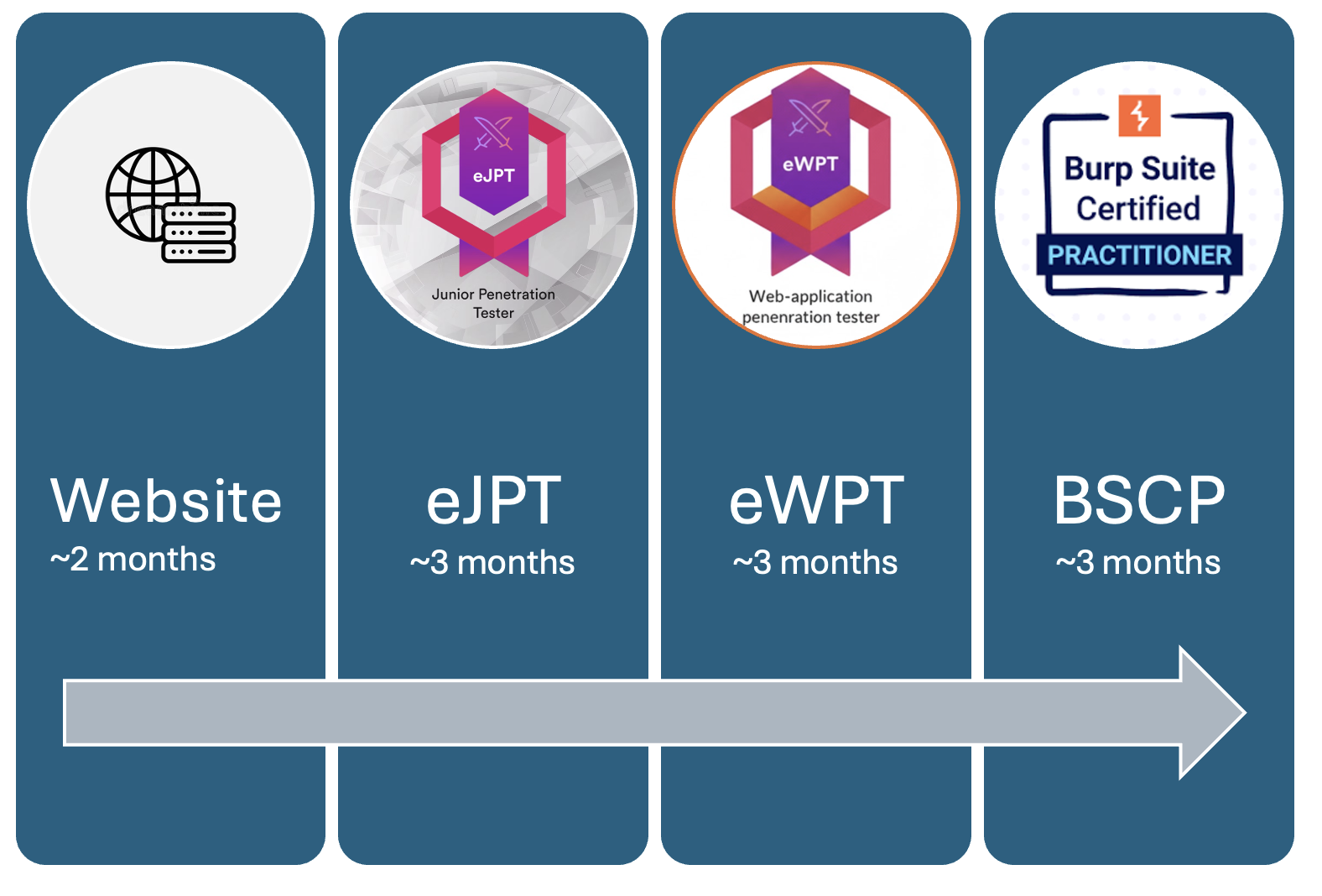
The following roadmap was developed to cultivate practical pentesting skills with an understanding of the fundemental concepts. The roadmap aims to establish real-world pentesting skills backed by industry-leading certifications.
1. Fundamentals
Building a Website
Building a website is one of the best ways to gain foundational knowledge for penetration testing, even though it doesn’t look like “security” at first.
Understanding How the Web Actually Works
When you build a website, you learn how the browser, server, and database interact with each other. This includes:
2. eJPT
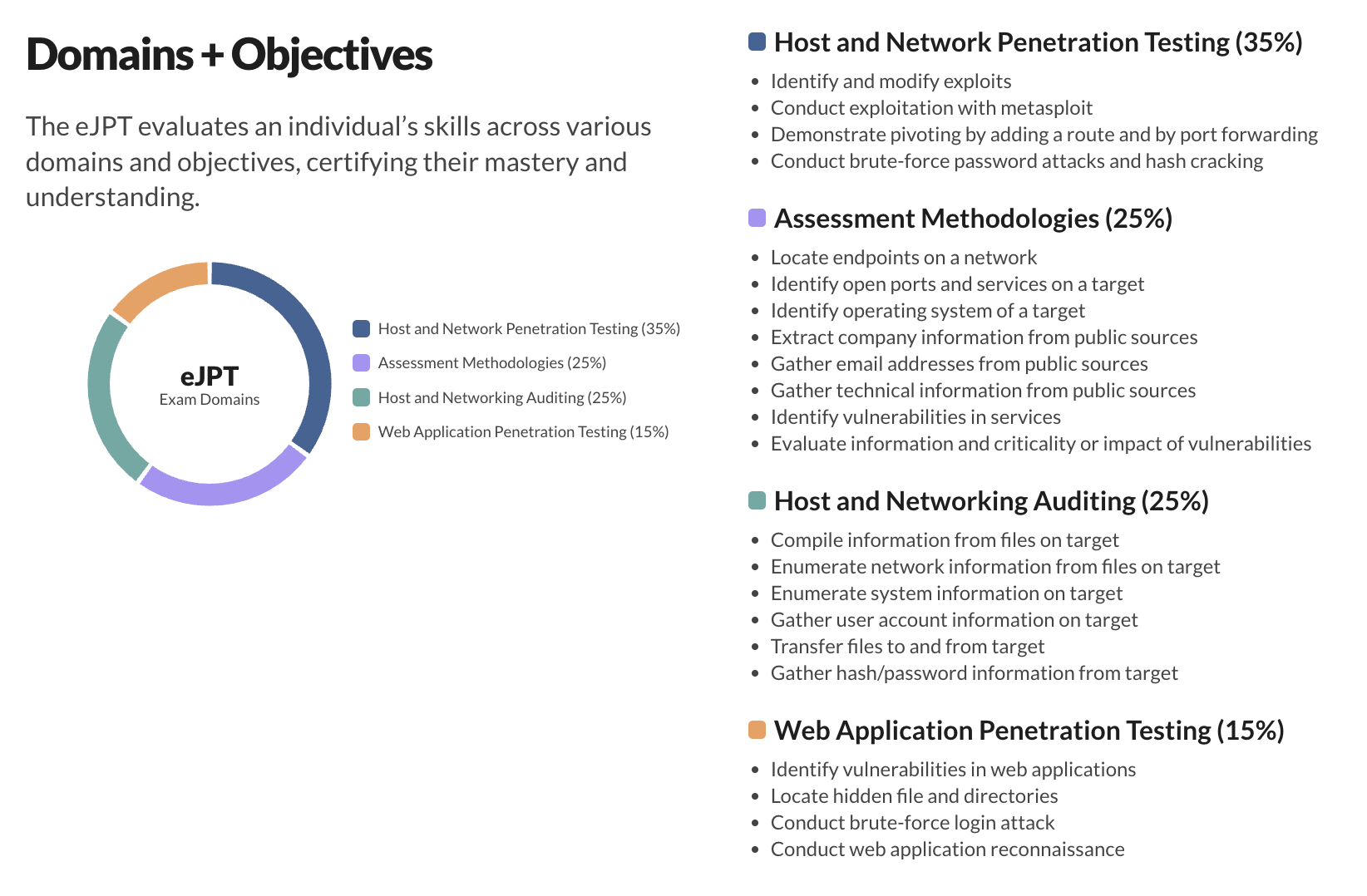
Once strong foundations are built in the web domain and there is a complete understanding of how websites work. The next step is exposure to security concepts and building a core pentesting methedology. The eJPT is a certification with more than 148-hours of training content and a 48 hour exam which provides real-world pentesting capabilities.
The eJPT introduces the following concepts:
- The phases of a penetration test
- How to approach a target systematically
- How to move from information gathering to testing
The eJPT (eLearnSecurity Junior Penetration Tester) is important for pentesting because it provides structure, fundamentals, and real-world context at the very beginning of a pentester’s journey. Mimicking real-world scenarios and packed with dozens of practical labs, the eJPT builds skills required for hands-on engagements and affirms the individual’s capability to become an asset in any penetration testing team.
The exam is 48 hrs with 35 questions. There are 5–6 machines in DMZ and 1–2 machines in the internal network. You are required to pivot from the DMZ to the internal network and also escalate your priviledges.
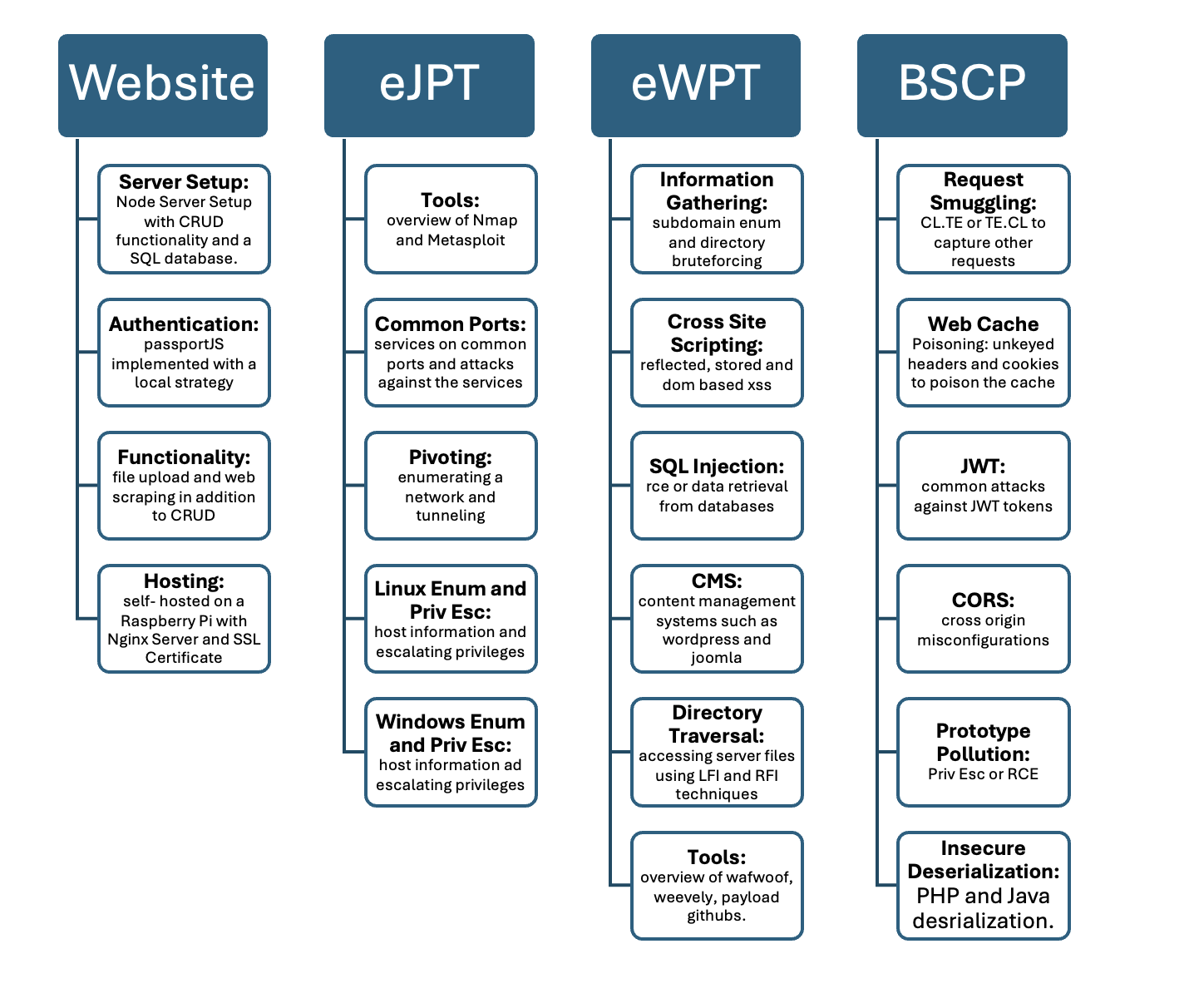
Curriculum
Notes:
- Tools
- Common Port
- Pivoting
- Linux Enumeration and Priviledge Escalation
- Windows Enumeration and Priviledge Escalation
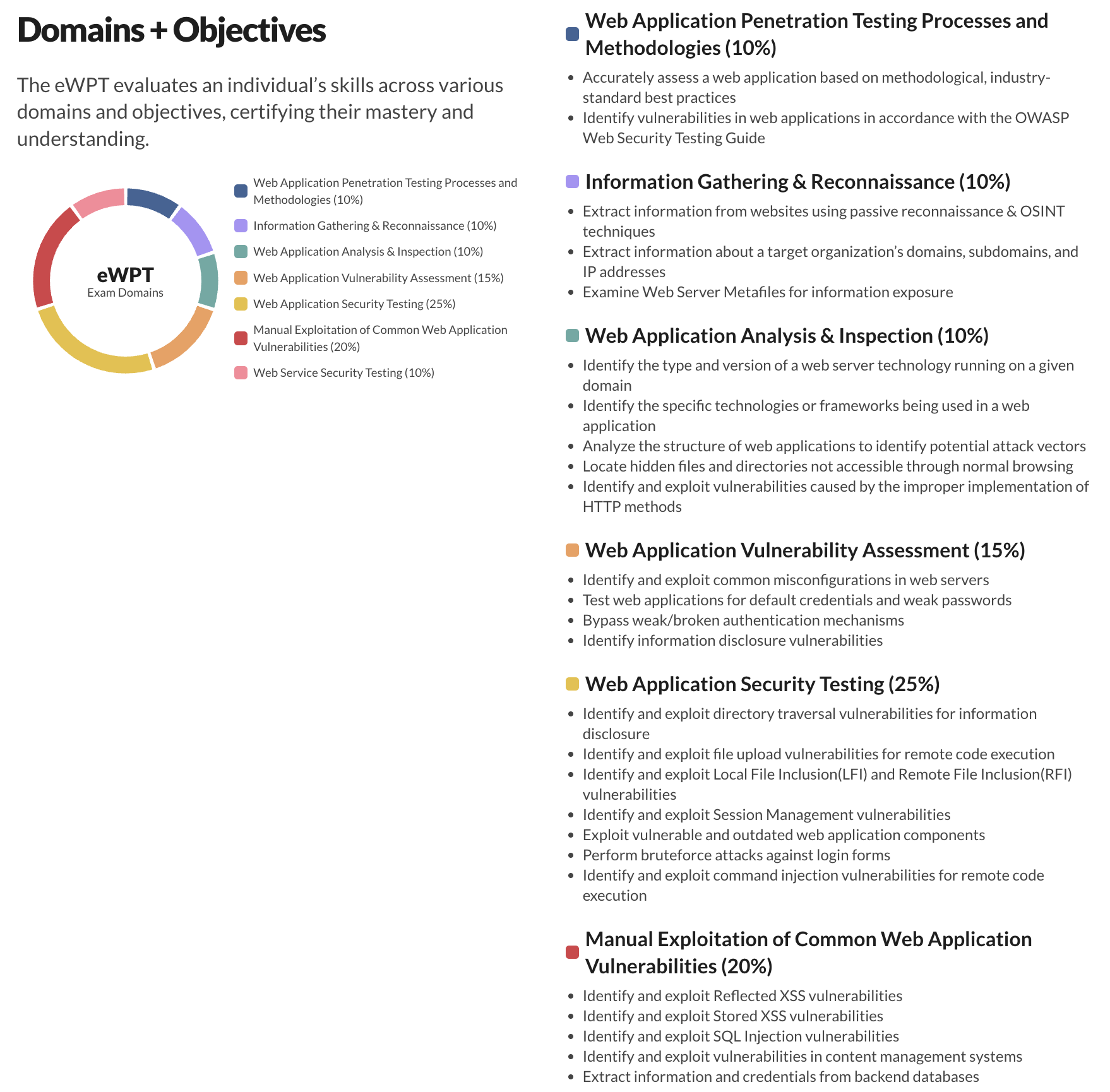
3. eWPT
eWPT is a hands-on, professional-level Red Team certification that simulates skills utilized during real-world engagements. The exam environment presents a scenario of a web application pentests that you need to perform on a collection of end-points. You have 10 hours to test the applications and services found in scope and 50 questions to answer in that time. You will need an overall passing score of 75% or above to pass the exam. The questions consist of multiple choice and short answer questions. These are contextual to the exam environment and may change between exams as it produces dynamic ‘flags’ to collect. Make no mistake, this is not a CTF style exam. You need to perform a pentest to uncover the answers.
Curriculum
Notes:
- Information Gathering
- Cross Site Scripting
- SQL Injection
- Content Management Systems
- Directory Traversal
- Tools
4. BSCP
The Burp Suite Certified Practitioner (BSCP) is an official certification for web security professionals, from the makers of Burp Suite. Becoming a Burp Suite Certified Practitioner demonstrates a deep knowledge of web security vulnerabilities. The certification consist of a collection of 300+ labs which provide a practical skills to master in-depth knowledge of web application attacks.
Curriculum
Advanced Topics:
- Insecure Deserialization
- Web LLM Attacks
- GraphQL API Vulnerabilities
- Server-Side Template Injection
- Web Cache Poisoning
- HTTP Host Header Attacks
- HTTP Request Smuggling
- OAuth Authentication
- JWT Attacks
- Prototype Pollution
Notes:
- Request Smuggling
- Web Cache Attacks
- JWT / OAuth Attacks
- Cross Origin Resource Sharing
- Prototype Pollution
- Insecure Deserialization
Conclusion
This roadmap represents a strong foundation in both web development and penetration testing, starting from building a solid understanding of how websites work, then progressing through structured learning paths such as eJPT, eWPT, and BSCP. However, it’s important to understand that penetration testing is a field of continuous learning. This roadmap is not the end, but rather a starting point. Future topics to expand this roadmap include Active Directory and Mobile Security.